[ad_1]
A few weeks in the past, I checked out the use of Google’s reCAPTCHA to dam junk mail in my Dig Deep Health web site. In keeping with that publish, Alex Skinner prompt that I glance into Cloudflare Turnstile. I wasn’t having any problems with reCAPTCHA. However, I do love Cloudflare as an organization; so, I figured it would be a laugh to have a look. Here is a fast demo of the use of Cloudflare Turnstile to be able to block junk mail in ColdFusion.
Turnstile is, roughly, a drop-in alternative for reCAPTCHA. In reality, they also have a reCAPTCHA-compatibility mode. However, for the sake of the exploration, I simply wish to get started from scratch.
As with reCAPTCHA, the Cloudflare Turnstile workflow comprises each server-side and client-side facets. At the client-side, a Cloudflare script makes a faraway API name to be able to provision a problem token. This token is then submitted along side your shape (the only that you are attempting to give protection to). And, as soon as the request is being processed at the ColdFusion server, we need to make a faraway API name again to the Clouldflare server to be able to examine the problem token.
Not like the reCAPTCHA verification workflow, which returns a ranking between 0–1, the Cloudflare Turnstile workflow merely returns a luck flag. This can be a minor distinction; however, it is as soon as much less factor that I’ve to consider as a developer, which is sweet.
Let’s get started this exploration at the ColdFusion aspect. When speaking with the Cloudflare API, I’m spreading the common sense throughout two other issues: coping with the low-level HTTP mechanics; and, decoding the Cloudflare reaction.
The low-level HTTP mechanics are treated via a ColdFusion element which is little greater than a glorified wrapper across the CFHttp tag. For this demo, I best want a unmarried means, siteVerify(), which submits the problem token again to Cloudflare API for verification.
On this ColdFusion element, and next parts, I will be the use of the CFProperty tag to outline accessor hooks. I am the use of this method, as a substitute of constructor injection, for Inversion of Keep an eye on (IoC).
element
accessors = true
output = false
trace = "I supply low-level HTTP get admission to to the Cloudflare Turnstile API."
{
// Outline houses for dependency-injection.
belongings identify="apiKey";
belongings identify="httpUtilities";
belongings identify="timeoutInSeconds" default=5;
// ---
// PUBLIC METHODS.
// ---
/**
* I examine the given Cloudflare Turnstile problem token.
*/
public struct serve as siteVerify(
required string token,
required string ipAddress,
numeric timeoutInSeconds = variables.timeoutInSeconds
) {
cfhttp(
consequence = "native.httpResponse",
means = "publish",
url = "https://demanding situations.cloudflare.com/turnstile/v0/siteverify",
getAsBinary = "sure",
timeout = timeoutInSeconds
) {
cfhttpparam(
sort = "formfield",
identify = "secret",
price = apiKey
);
cfhttpparam(
sort = "formfield",
identify = "reaction",
price = token
);
cfhttpparam(
sort = "formfield",
identify = "remoteip",
price = ipAddress
);
}
var fileContent = httpUtilities.getFileContentAsString( httpResponse );
if ( httpUtilities.isFailureResponse( httpResponse ) ) {
throw(
sort = "Turnstile.Gateway.ApiFailure",
message = "Cloudflare Turnstile API error.",
element = "Returned with standing code: #httpResponse.statusCode#",
extendedInfo = fileContent
);
}
check out {
go back( deserializeJson( fileContent ) );
} catch ( any error ) {
throw(
sort = "Turnstile.Gateway.PayloadError",
message = "Cloudflare Turnstile API reaction intake error.",
element = "Returned with standing code: #httpResponse.statusCode#",
extendedInfo = fileContent
);
}
}
}
As you’ll be able to see, this ColdFusion element does not anything greater than orchestrate the HTTP request to the Cloudflare API and try to deserialize the JSON reaction. In line with the documentation, the minimum JSON reaction seems like this:
{
"luck": true,
"error-codes": [],
"challenge_ts": "2022-10-06T00:07:23.274Z",
"hostname": "instance.com"
}
However, it seems like further information may also be equipped to be able to supply extra context concerning the workflow being secure. I’ve no longer attempted the use of the non-compulsory information but.
Eating the API reaction is then the duty of the TurnstileClient.cfc. In terms of executing instructions towards my ColdFusion programs, I generally tend to make use of an exception-driven keep an eye on drift. This is, I suppose that each one portions of the “glad trail” paintings; and, I permit each and every step to throw an error to be able to halt processing.
To that finish, my TurnstileClient.cfc has two strategies: testToken() and verifyToken(). The verifyToken() means invokes the low-level HTTP request and returns the luck flag. The testToken() means then wraps the verifyToken() means and throws an error if the problem token will get rejected.
element
accessors = true
output = false
trace = "I supply high-level HTTP get admission to to the Cloudflare Turnstile API."
{
// Outline houses for dependency-injection.
belongings identify="gateway";
// ---
// PUBLIC METHODS.
// ---
/**
* I take a look at the given Cloudflare Turnstile problem token supplied via the client-side
* shape. If the problem passes effectively, this technique exits. Differently, it throws
* an error.
*/
public void serve as testToken(
required string token,
required string ipAddress
) {
if ( ! verifyToken( argumentCollection = arguments ) ) {
throw(
sort = "Turnstile.Shopper.VerificationFailure",
message = "Cloudflare Turnstile verification failure.",
element = "Problem didn't move, person could be a bot."
);
}
}
/**
* I examine the given Cloudflare Turnstile problem token.
*/
public boolean serve as verifyToken(
required string token,
required string ipAddress
) {
// If no token has been supplied via the Turnstile gadget, then we all know that the
// person is trying to circumvent the safety. There is not any wish to make the API
// name (be aware: it is conceivable that the person simply submitted the shape too temporarily).
if ( ! token.len() ) {
throw(
sort = "Turnstile.Shopper.InvalidToken",
message = "Cloudflare Turnstile token is empty."
);
}
var apiResponse = gateway.siteVerify( token, ipAddress );
go back( apiResponse.luck );
}
}
This TurnstileClient.cfc is the ColdFusion element that we are going to eat in our shape submission. And, the testToken() means is the process we’re going to invoke all the way through our shape processing.
At the client-side, I am the use of Cloudflare’s implicit rendering method. That is the place I load the Turnstile script and feature it mechanically provision a problem token and inject the token into the shape as a hidden enter. It does this via searching for a component with the CSS elegance identify, cf-turnstile. As soon as this component is located, Cloudflare renders the Turnstile widget as the primary kid (of this component); after which, appends a hidden enter as a next kid that encodes the problem token.
Apart: Cloudflare supplies particular rendering tactics if you wish to have granular keep an eye on over when the problem token is provisioned and the way it interacts with the shape. However, I don’t want that point of keep an eye on at the moment.
For the sake of simplicity, I’ll instantiate a brand new example of my ColdFusion parts on the height of each web page:
<cfscript>
// SECURITY CAUTION: You must no longer display the SECRET KEY to someone. This can be a set of
// throw-away keys (configured for "localhost") that I've created in particular for
// this demo.
config = {
siteKey: "0x4AAAAAAAPqhac0_y9Coyz-",
secretKey: "0x4AAAAAAAPqhVYA58LIIuKHIa4q4b6Fp2c"
};
// The usage of Inversion of Keep an eye on (IoC) to create the gateway element after which supply
// it to the Cloudflare Turnstile Jstomer element as a dependency.
// --
// NOTE: Most often, I might cache this ColdFusion element in a chronic scope; however,
// for the sake of the demo and ease, I'm re-creating it on each request.
turnstileGateway = new TurnstileGateway()
.setApiKey( config.secretKey )
.setHttpUtilities( new HttpUtilities() )
;
turnstileClient = new TurnstileClient()
.setGateway( turnstileGateway )
;
// ------------------------------------------------------------------------------- //
// ------------------------------------------------------------------------------- //
param identify="shape.submitted" sort="boolean" default=false;
param identify="shape.username" sort="string" default="";
param identify="shape.password" sort="string" default="";
// This box is mechanically populated via the client-side Cloudflare Turnstile
// problem. The usage of the IMPLICIT rendering method, Cloudflare's script will
// mechanically generate a problem token and populate a hidden enter box.
param identify="shape[ 'cf-turnstile-response' ]" sort="string" default="";
errorMessage = "";
if ( shape.submitted ) {
check out {
// NOTE: Each and every Cloudflare Turnstile problem token is legitimate for 5-minutes and
// can best be verified as soon as to be able to save you replay assaults.
turnstileClient.testToken(
token = shape[ "cf-turnstile-response" ],
ipAddress = cgi.remote_addr
);
// TODO: Exact authentication common sense for the applying ...
location(
url = "./house.cfm",
addToken = false
);
} catch ( any error ) {
transfer ( error.sort ) {
case "Turnstile.Shopper.InvalidToken":
case "Turnstile.Shopper.VerificationFailure":
errorMessage = "Your login shape has expired. Please check out filing your shape once more.";
smash;
default:
errorMessage = "An surprising error happened."
smash;
}
}
} // END: Submitted.
</cfscript>
<cfoutput>
<!doctype html>
<html lang="en">
<head>
<meta charset="utf-8" />
<meta identify="viewport" content material="width=device-width, initial-scale=1" />
</head>
<frame>
<h1>
Cloudflare Turnstile Demo In ColdFusion
</h1>
<cfif errorMessage.len()>
<p>
<robust>Error:</robust> #encodeForHtml( errorMessage )#
</p>
</cfif>
<shape means="publish">
<enter sort="hidden" identify="submitted" price="true" />
<p>
<robust>Username:</robust><br />
<enter sort="textual content" identify="username" dimension="30" />
</p>
<p>
<robust>Password:</robust><br />
<enter sort="password" identify="password" dimension="30" />
</p>
<p>
<button sort="publish">
I am utterly a Human, Login!
</button>
</p>
<!--- Turnstile problem widget is rendered as a kid of this DIV. --->
<div
data-sitekey="#encodeForHtmlAttribute( config.siteKey )#"
elegance="cf-turnstile"
taste="margin-top: 30px ;">
<!---
NOTE: This div should be throughout the FORM as it's going to inject a hidden shape
box as a kid component (which should be submitted to the server).
--->
</div>
</shape>
<!---
Load Cloudflare Turnstile script. Since I am the use of the implicit rendering
method, it's going to mechanically search for the component with the category identify
"cf-turnstile", render the widget there, after which inject the problem token
as a hidden enter box.
--->
<script
src="https://demanding situations.cloudflare.com/turnstile/v0/api.js"
async defer>
</script>
</frame>
</html>
</cfoutput>
As you’ll be able to see, with the implicit rendering method, I haven’t any JavaScript. I merely come with the Cloudflare script and serve-up a component with the category identify, cf-turnstile. Cloudflare looks after the remaining (from a client-side point of view). Then, at the ColdFusion server, I am taking the provisioned problem token and I am trying out it with my TurnstileClient.cfc. And, if the take a look at passes, I continue with the shape submission.
If I then open this ColdFusion web page within the browser, we see the Cloudflare widget get rendered:
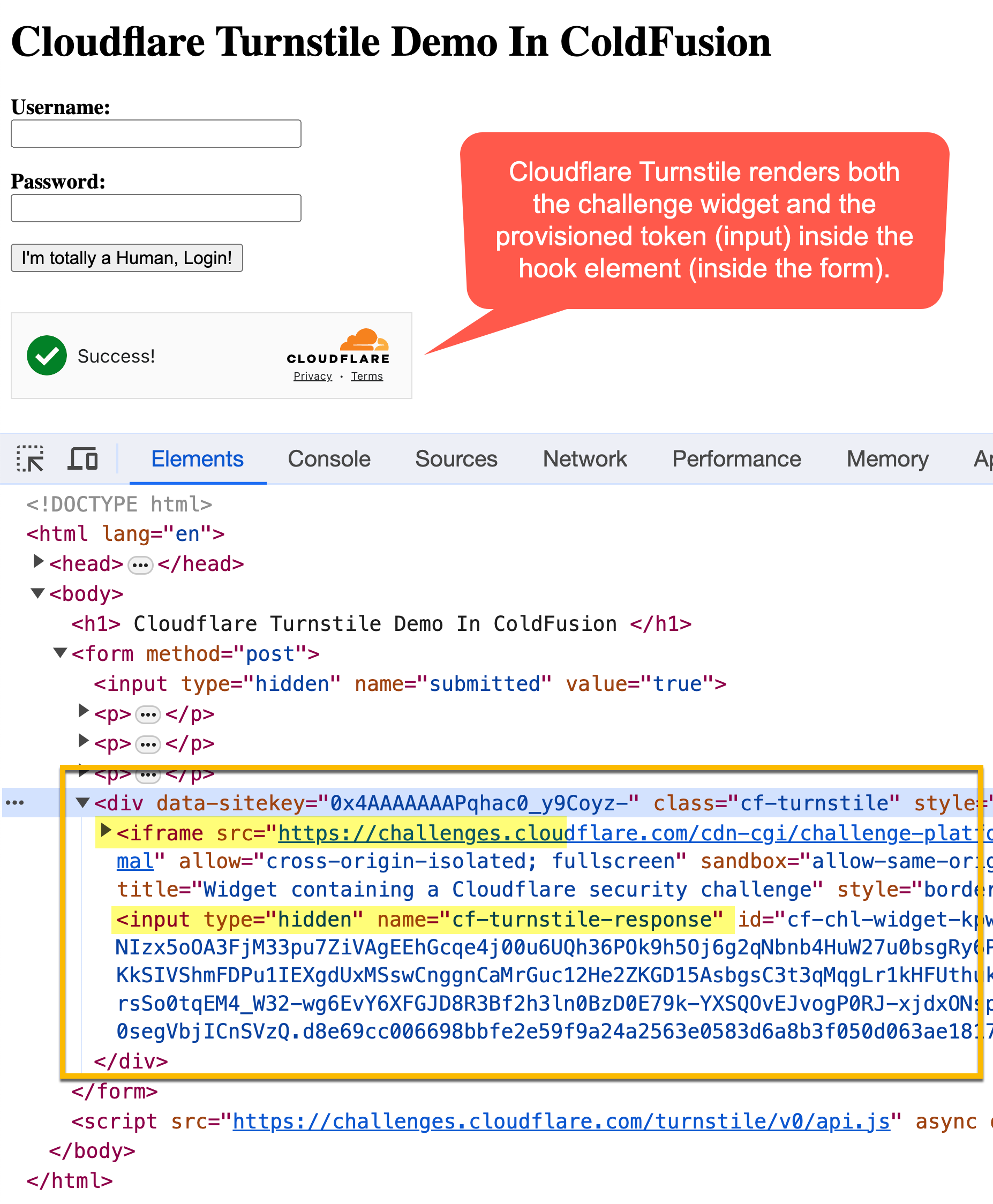
As you’ll be able to see, our empty div with elegance identify, cf-turnstile, finally ends up containing each the problem widget (as an iframe) and the hidden enter that comprises the problem token. And, since that is all being rendered throughout the <shape> tag, the problem token is submitted to the ColdFusion server along side the login credentials.
In the event you evaluate this weblog publish to the former one (about Google reCAPTCHA), the code seems nearly precisely the similar in each demos. Which is sensible for the reason that workflows are precisely the similar; and, Cloudflare Turnstile was once designed to be a alternative for CAPTCHA. The foremost distinction (in my two demos) is that I broke the HTTP helper utilities out into their very own ColdFusion element. This type of refactoring is not important for the demo; however, it extra carefully mirrors what I would do in a manufacturing environment:
element
output = false
trace = "I supply not unusual application purposes for eating HTTP responses."
{
/**
* I go back the given fileContent payload a UTF-8 encoded string. Despite the fact that we ask for a
* request to go back the fileContent as a Binary price, the kind is best assured if
* the request comes again correctly. If one thing is going extraordinarily incorrect (comparable to a
* "Connection Failure"), the fileContent will nonetheless be returned as a easy string.
* This technique will normalize each reaction instances to a string.
*/
public string serve as getFileContentAsString( required struct httpResponse ) {
if ( isBinary( httpResponse.fileContent ) ) {
go back( charsetEncode( httpResponse.fileContent, "utf-8" ) );
}
go back( httpResponse.fileContent );
}
/**
* I decide if the given HTTP reaction has a failure / non-2xx standing code.
*/
public boolean serve as isFailureResponse( required struct httpResponse ) {
go back( ! isSuccessResponse( httpResponse ) );
}
/**
* I decide if the given HTTP reaction has a luck / 2xx standing code.
*/
public boolean serve as isSuccessResponse( required struct httpResponse ) {
go back( httpResponse.statusCode.reFind( "2dd" ) );
}
}
I simply deployed this transformation to Dig Deep Health this morning and to this point the whole lot appears to be operating easily. In the previous few hours, I have never noticed any junk mail shape submissions get via!
Wish to use code from this publish?
Take a look at the license.
[ad_2]